What Is Pretexting Definition Examples And Attacks Fortinet

What Is Pretexting Definition Examples And Attacks Fortinet Pretexting definition. pretexting is a form of social engineering tactic used by attackers to gain access to information, systems, or services by creating deceptive scenarios that increase the success rate of a future social engineering attack. social engineering refers to when a hacker impersonates someone the victim knows or trusts—such as. Pretexting is form of social engineering in which an attacker tries to convince a victim to give up valuable information or access to a service or system. the distinguishing feature of this kind.
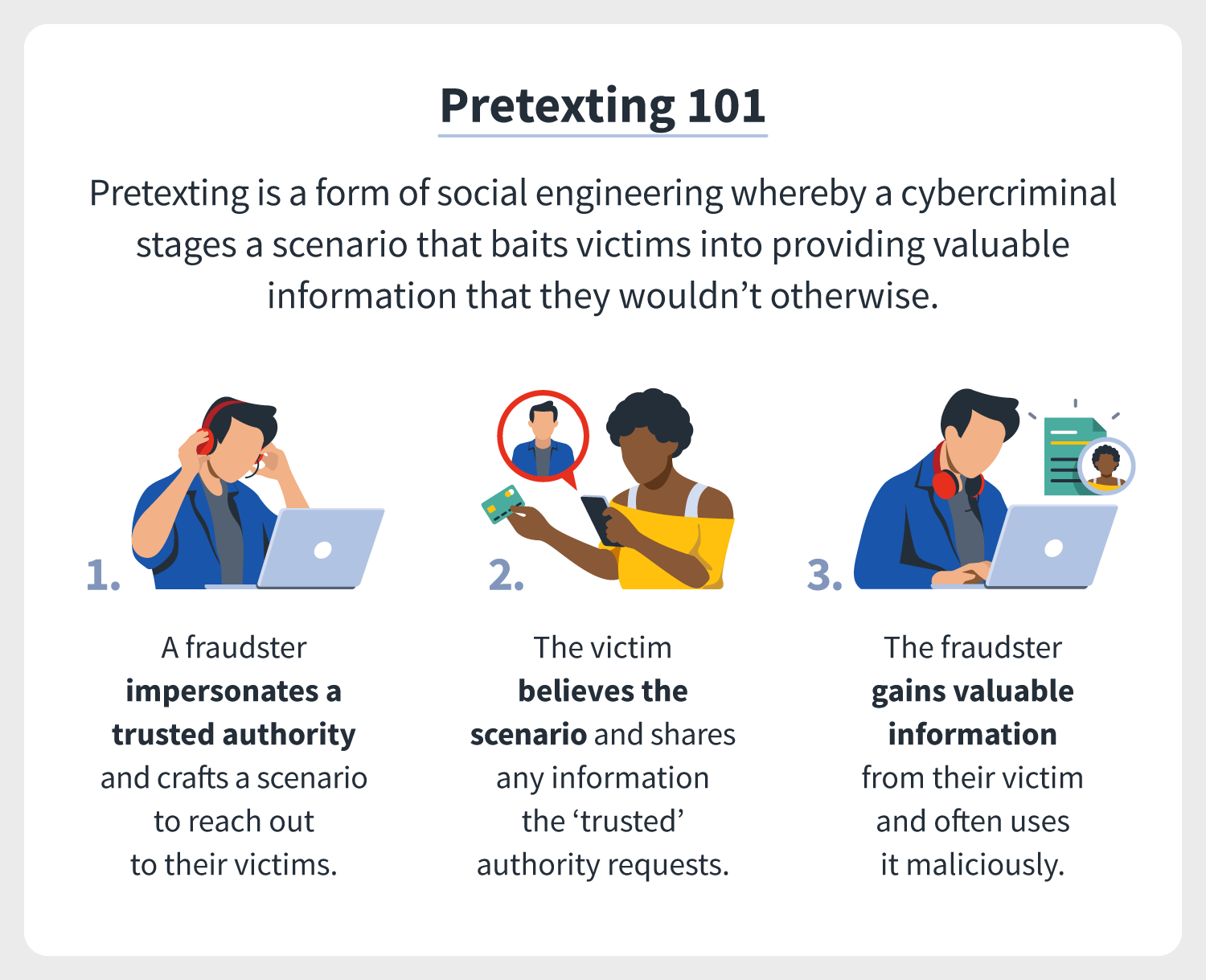
What Is Pretexting Definition Examples Prevention Tips Norton Pretexting is a form of social engineering attack in which a scammer creates a plausible scenario to bait victims into divulging sensitive information, making fraudulent payments, granting access to an account, and so on. closely related to various types of phishing, pretexting scams are characterized by detailed situations (pretexts) and often. A “pretext” is a false reason or story used to conceal one’s true intentions. in cybersecurity, pretexting is the use of a fake story to trick someone into giving up important data or performing a target action. think you can spot a pretexting attack? they can be incredibly deceitful—and the fallout can be devastating. Below are a few specific examples of steps you can take to prevent an attack causing damage to you or your business. here’s how to avoid a pretexting attack: establish security protocols, policies, and procedures for handling sensitive information. do not divulge sensitive information to unverified entities via email, phone, or text messages. Pretexting is a social engineering attack where the attacker creates a fabricated identity or scenario to persuade a victim to divulge confidential information, grant access to restricted systems, or perform actions they would otherwise not undertake. unlike phishing attacks that often rely on inducing panic or urgency, pretexting typically.
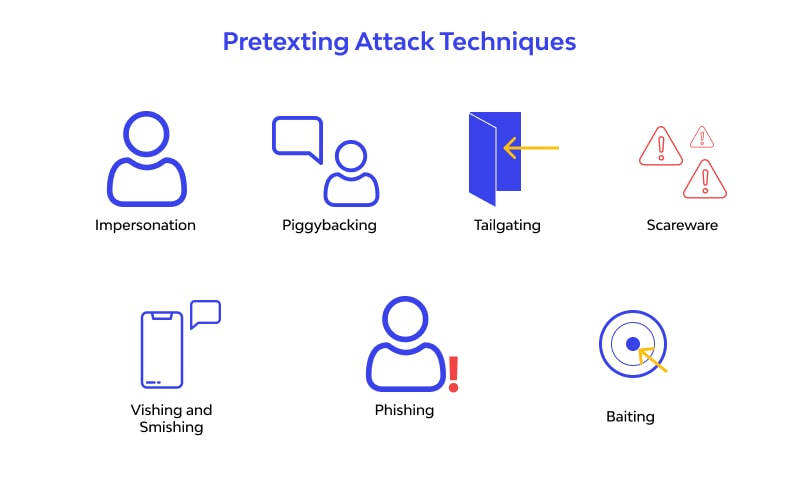
ççwhat Is Pretexting çü ôÿø å ççattack çü ççdefinition çü Meaning ççexamples çü Below are a few specific examples of steps you can take to prevent an attack causing damage to you or your business. here’s how to avoid a pretexting attack: establish security protocols, policies, and procedures for handling sensitive information. do not divulge sensitive information to unverified entities via email, phone, or text messages. Pretexting is a social engineering attack where the attacker creates a fabricated identity or scenario to persuade a victim to divulge confidential information, grant access to restricted systems, or perform actions they would otherwise not undertake. unlike phishing attacks that often rely on inducing panic or urgency, pretexting typically. Pretexting is a social engineering technique where attackers create a phony story, or "pretext," to deceive victims into providing valuable information or granting them access to something important. bad actors often pose as authority figures or someone who can assist the victim when using this technique. A pretexting attack is a type of social engineering attack where the threat actor persuades their target into revealing sensitive information or sending them money by making up a story, hence the word “pretext.”. pretexting attacks can come in many different forms including a phone call, text message, email or even in person.

Comments are closed.