Understanding Network Security Tools Protection Ir

Understanding Network Security Tools Protection Ir The term 'network security' is an all encompassing, umbrella concept that describes different types of software and hardware solutions. it also refers to the processes or security rules and configurations relating to network use, secure network access, and overall threat protection within company networks. In our latest blog, ir's tony smith explore how msps can stay on top of their clients’ needs, build long term trust, and ensure mutual growth. bit.ly 4bzy6hd unlocking revenue growth for.
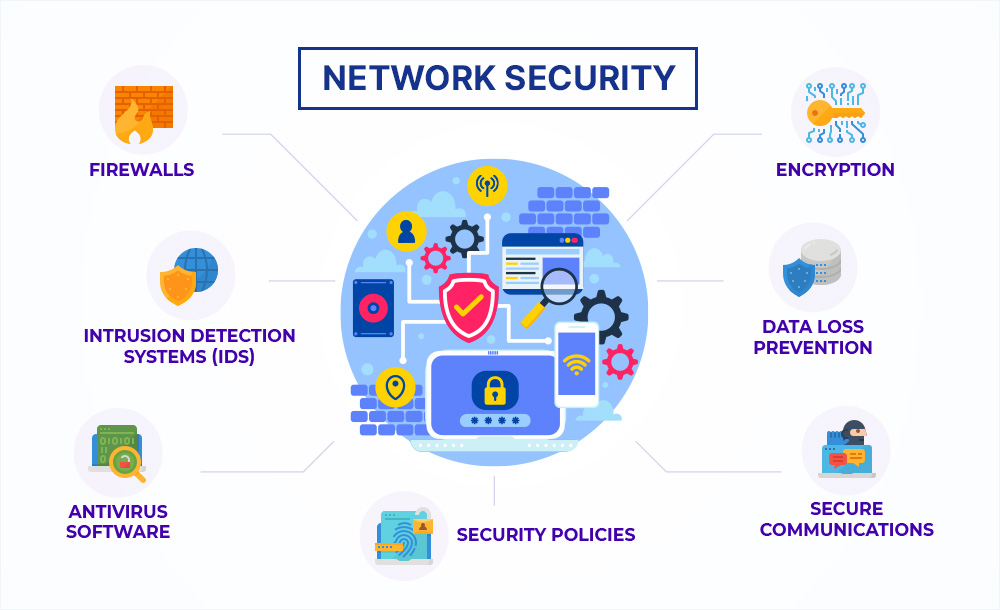
Understanding Network Security Tools Protection Ir A virtual private network (vpn) is a security tool that encrypts the connection from an endpoint to an organization’s network, allowing authorized users to safely connect and use the network from a remote setting. vpns usually leverage advanced authentication methods to ensure both the device and user are authorized to access the network. Virtual private network (vpn) vpn security tools are used to authenticate communication between secure networks and an endpoint device. remote access vpns generally use ipsec or secure sockets layer (ssl) for authentication, creating an encrypted line to block other parties from eavesdropping. web security. 10 essential security tools. 1. network access control (nac) nac products allow enterprises to enforce security policies on devices and users attempting to access their network. nac products can. Ensure the ir team has the appropriate skills and training. this includes exercising the ir plan from time to time. it also includes staffing the ir team, with either in house staff or through a third party provider, to accommodate the time away from the job necessary in order to maintain certifications and leverage other educational opportunities.

Understanding Network Security Tools Protection Ir 10 essential security tools. 1. network access control (nac) nac products allow enterprises to enforce security policies on devices and users attempting to access their network. nac products can. Ensure the ir team has the appropriate skills and training. this includes exercising the ir plan from time to time. it also includes staffing the ir team, with either in house staff or through a third party provider, to accommodate the time away from the job necessary in order to maintain certifications and leverage other educational opportunities. The safest strategy for network security is to use a combination of security tools, including protection for endpoints and internet connections. many cybersecurity systems providers offer platforms of modules that work together to close off all possible attack strategies – crowdstrike falcon is an example of this. Network security architecture is a strategy that provides formal processes to design robust and secure networks. effective implementation improves data throughput, system reliability, and overall.

Understanding Network Security Tools Protection Ir The safest strategy for network security is to use a combination of security tools, including protection for endpoints and internet connections. many cybersecurity systems providers offer platforms of modules that work together to close off all possible attack strategies – crowdstrike falcon is an example of this. Network security architecture is a strategy that provides formal processes to design robust and secure networks. effective implementation improves data throughput, system reliability, and overall.

Understanding Network Security Tools Protection Ir

Comments are closed.