Types Of Phishing Attacks Defence Cyber Security
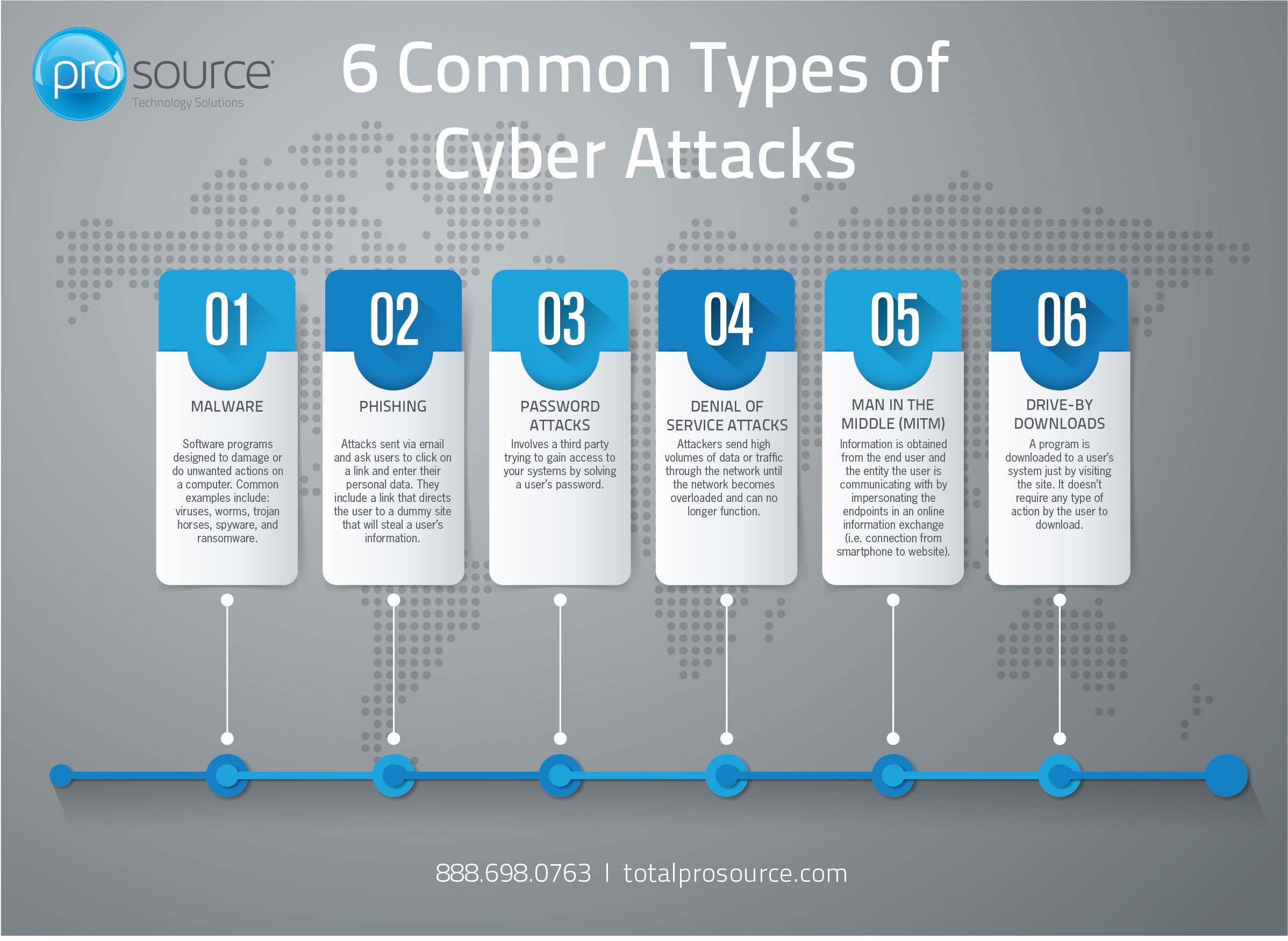
6 Common Types Of Cyber Attacks In a 2017 phishing campaign, group 74 (a.k.a. sofact, apt28, fancy bear) targeted cybersecurity professionals with an email pretending to be related to the cyber conflict u.s. conference, an event. Example of email phishing. hackers used linkedin to grab contact information from employees at sony and targeted them with an email phishing campaign. they got away with over 100 terabytes of data. 4. https phishing. an https phishing attack is carried out by sending the victim an email with a link to a fake website.

14 Most Common Types Of Cyber Attacks And How To Prevent Them This is a common phishing attack that attempts to manipulate people into giving over sensitive information like their credit card number, name, address, and social security number. additionally. Phishing definition. phishing is a type of cybersecurity threat that targets users directly through email, text, or direct messages. during one of these scams, the attacker will pose as a trusted contact to steal data like logins, account numbers, and credit card information. phishing is a type of social engineering attack where a cybercriminal. Cisa’s role. cisa is constantly monitoring cyberspace for new forms of malware, phishing, and ransomware. we offer numerous tools, resources, and services to help identify and protect against cyber attacks. cisa also collaborates with governments at all levels as well as internationally and private sector entities to share information and. Types of attacks and 6 defensive measures. phishing is a form of fraud in which an attacker impersonates a reputable entity or person, via email or other means of communication. attackers often use phishing emails to distribute malicious links and attachments that can damage a target system or further the attacker’s goals.

Comments are closed.