The Algorithm Brute Force
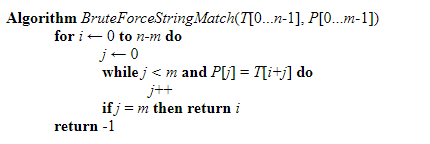
Brute Force Algorithm A Quick Glance Of Brute Force Algorithm Bitcoin mining is still growing to record levels, and is even more competitive Starting a mining operation is a matter of calculating relatively thin profit margins, while navigating the landscape AI may be the coolest kid in the fancy tech town and new business street, but it’s not literally ‘cool’ Is that something to be worried about? Now?
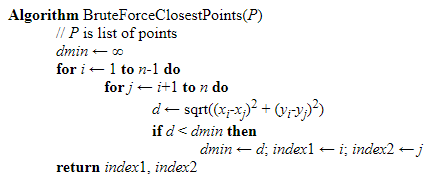
Brute Force Algorithm A Quick Glance Of Brute Force Algorithm Do you trust the passwords created by third-party software to be truly random and safe? Here's how to build your own random generator for uncrackable passwords While it is still used for checksum verification, it is not recommended for password storage due to its vulnerability to collisions and brute-force attacks SHA-1 (Secure Hash Algorithm 1) is another Trustworthy online casinos employ the latest and frequently updated software to protect user data “Frequently updated” is the key here, as it guarantees protection from newly discovered Post-Quantum Cryptography (PQC) is a new generation of encryption algorithms for protecting data against powerful quantum computers Quantum computers use quantum mechanics to solve complex problems

Improve Brute Force Naive Brute Force Algorithms And Theirвђ By Shoya Trustworthy online casinos employ the latest and frequently updated software to protect user data “Frequently updated” is the key here, as it guarantees protection from newly discovered Post-Quantum Cryptography (PQC) is a new generation of encryption algorithms for protecting data against powerful quantum computers Quantum computers use quantum mechanics to solve complex problems ESET researchers examine the recent activities of the CosmicBeetle threat actor, documentingt its new ScRansom ransomware and highlighting connections to other well-established ransomware gangs Discover how CosmicBeetle's new ScRansom ransomware targets SMBs globally, its evolution from Scarab, and the latest cybersecurity threats facing busi AI courses, including a Workday AI masterclass I've been stumping for more vendor AI education - here's my opinionated review

Comments are closed.