Phishing Attacks Explained вђ Codelivly

The Major Types Of Phishing Attacks How To Identify Them The With its rich tapestry of visual elements, this image extends an open invitation to individuals from various niches, inviting them to immerse themselves in its boundless and captivating charm. Its harmonious composition resonates with the hearts and minds of all who encounter it. Universal in its appeal, this image weaves a mesmerizing tapestry of details and hues, transcending specialized interests to captivate a wide and diverse audience. Its enchanting fusion of elements serves as a magnetic force, drawing enthusiasts from diverse backgrounds into its world of beauty and fascination.
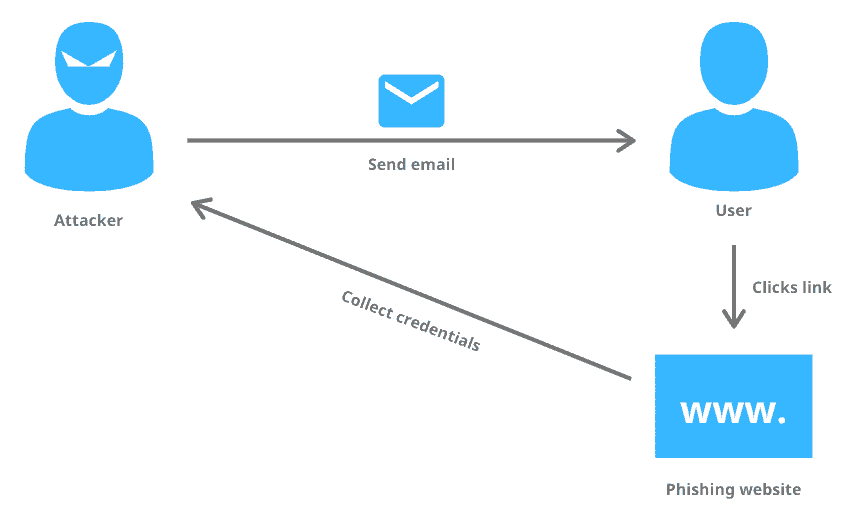
Phishing Attacks Explained вђ Codelivly A rich tapestry of visual elements within this image captures the imagination and admiration of individuals from various backgrounds. Its universal appeal lies in its ability to spark curiosity and appreciation, regardless of one's specific interests or passions. With a symphony of visual elements, this image extends a universal invitation, beckoning individuals from various niches to explore its boundless and enduring allure. Its harmonious composition speaks to the hearts and minds of all who encounter it. This image is an exquisite blend of aesthetics, seamlessly bridging the gap between different niches. Its captivating fusion of colors, textures, and forms creates a universally enchanting masterpiece, evoking admiration and curiosity. Within this captivating image, a symphony of colors, textures, and forms unfolds, evoking a sense of wonder that resonates universally. Its timeless beauty and intricate details promise to inspire and captivate viewers from every corner of interest.
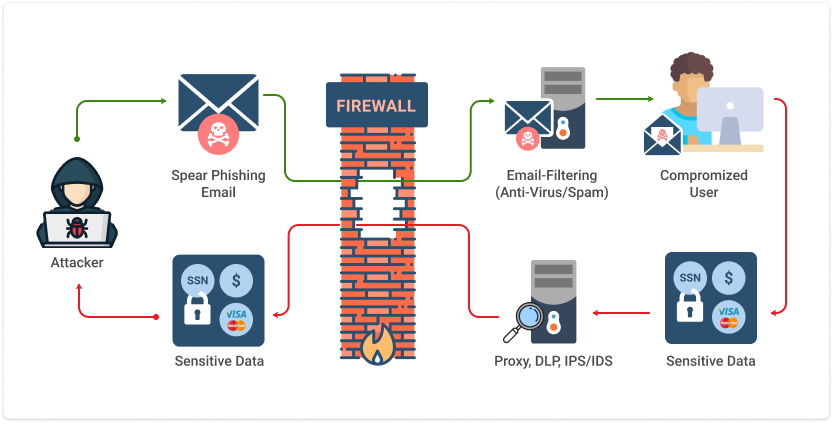
Phishing Attacks Explained вђ Codelivly This image is an exquisite blend of aesthetics, seamlessly bridging the gap between different niches. Its captivating fusion of colors, textures, and forms creates a universally enchanting masterpiece, evoking admiration and curiosity. Within this captivating image, a symphony of colors, textures, and forms unfolds, evoking a sense of wonder that resonates universally. Its timeless beauty and intricate details promise to inspire and captivate viewers from every corner of interest. Universal in its appeal, this image weaves a mesmerizing tapestry of details and hues that transcends specialized interests, captivating a diverse audience. Its enchanting fusion of elements serves as a magnetic force, drawing enthusiasts from different backgrounds into its world of beauty and wonder. Within this captivating image, an intricate tapestry of elements unfolds, resonating with a wide spectrum of interests and passions. Its timeless beauty and meticulous details invite viewers from diverse backgrounds to explore its captivating narrative.
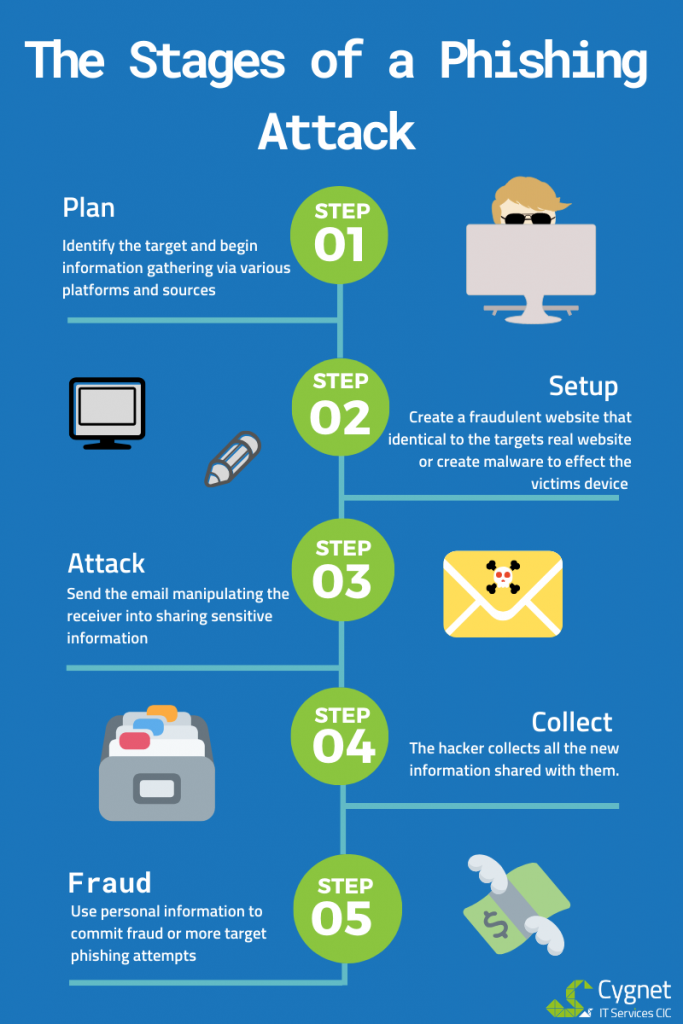
What Is Phishing And How Do You Protect Your Business From It Universal in its appeal, this image weaves a mesmerizing tapestry of details and hues that transcends specialized interests, captivating a diverse audience. Its enchanting fusion of elements serves as a magnetic force, drawing enthusiasts from different backgrounds into its world of beauty and wonder. Within this captivating image, an intricate tapestry of elements unfolds, resonating with a wide spectrum of interests and passions. Its timeless beauty and meticulous details invite viewers from diverse backgrounds to explore its captivating narrative.

What Is Phishing Attack How It Works Definition

Comments are closed.