Learn Windbg Typical X86 Call Stack Example

Learn Windbg Typical X86 Call Stack Example An example for typical x86 call stack . call stack is a stack data structure that saves information about function calls. each thread has its own stack where the thread maintains the history of its active function calls. the following picture shows an example of typical x86 call stack and its stack frames. To open the calls window, choose call stack from the view menu. the following screen shot shows an example of a calls window. buttons in the calls window enable you to customize the view of the call stack. to move to the corresponding call location in the source window or disassembly window, double click a line of the call stack, or select a.
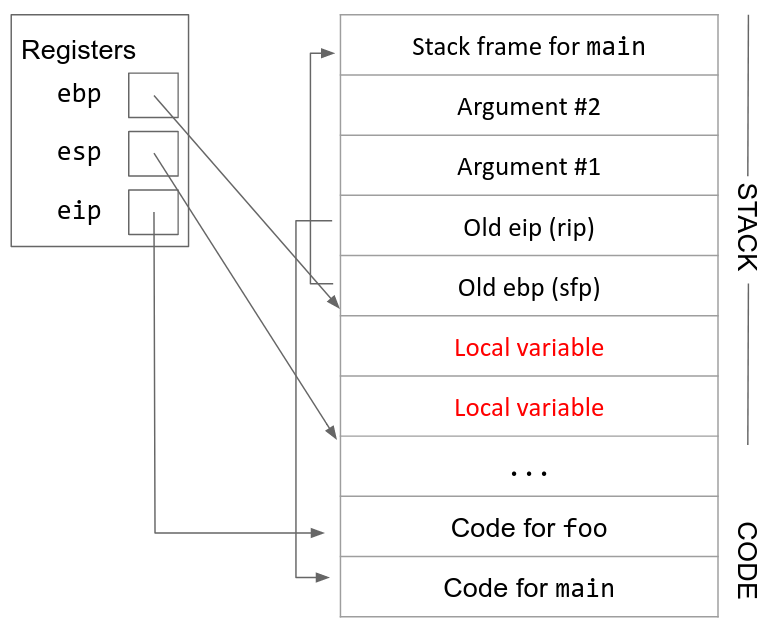
2 X86 Assembly And Call Stack Computer Security Open notepad and attach windbg. go to your installation directory, and open windbg.exe. on the file menu, select launch executable. in the launch executable dialog, go to the folder that contains notepad.exe. (the notepad.exe file usually is in c:\windows\system32.) for file name, enter notepad.exe. In any case, being able to manually walk a stack is often valuable. the basic concept is fairly simple: dump out the stack pointer, find out where the modules are loaded, find possible function addresses, and verify by checking to see if each possible stack entry makes a call to the next. before going through an example, it is important to note. Start windbg; open the dump file. (ctrl d by default) tell windbg to go get the correct microsoft symbol files. type .symfix. this may take a few moments as it will pull a ton of stuff down from the internet. tell windbg where the symbols (pdb files) are. type .sympath c:\pdblocation, substituting wherever you put the pdb files for the pathname. Below table shows the brief summary of x86 calling conventions in windows. cdecl. c c default calling convention. push parameters onto stack in the right to left order. caller cleans the stack. name decoration: foo. stdcall. most win32 apis use stdcall. push parameters onto stack in the right to left order.
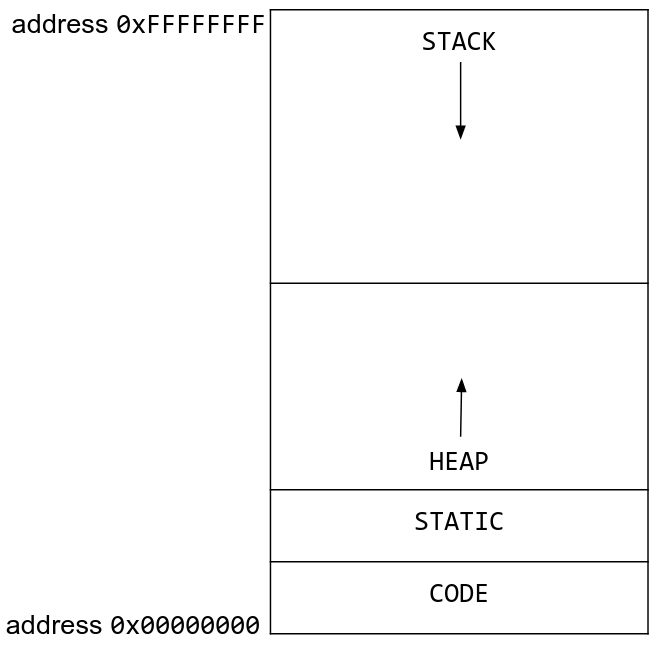
2 X86 Assembly And Call Stack Computer Security Start windbg; open the dump file. (ctrl d by default) tell windbg to go get the correct microsoft symbol files. type .symfix. this may take a few moments as it will pull a ton of stuff down from the internet. tell windbg where the symbols (pdb files) are. type .sympath c:\pdblocation, substituting wherever you put the pdb files for the pathname. Below table shows the brief summary of x86 calling conventions in windows. cdecl. c c default calling convention. push parameters onto stack in the right to left order. caller cleans the stack. name decoration: foo. stdcall. most win32 apis use stdcall. push parameters onto stack in the right to left order. A quick recap on some of the key points about x86 environment, that we have already discussed before in this series: ebp (frame pointer) of the previous frame is stored at ebp of current frame. Where is windbg.exe? typical x86 call stack example set breakpoint at source line msvc linker option : generate debug info simple stack overflow example simple buffer overrun example simple heap corruption example calling conventions.
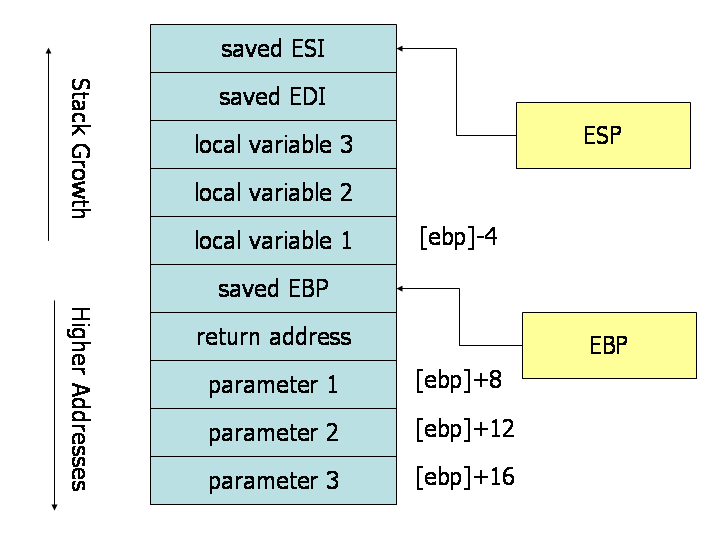
Guide To X86 Assembly A quick recap on some of the key points about x86 environment, that we have already discussed before in this series: ebp (frame pointer) of the previous frame is stored at ebp of current frame. Where is windbg.exe? typical x86 call stack example set breakpoint at source line msvc linker option : generate debug info simple stack overflow example simple buffer overrun example simple heap corruption example calling conventions.

Comments are closed.