How To Identify And Avoid Social Engineering Attacks Neuron Computers

How To Identify And Avoid Social Engineering Attacks Neuron Computers Here are the key methods to protect your business and users from social engineering attacks. understand the tactics being used. social engineering relies on standard psychological ploys that are designed to get the desired reaction from the subject. understanding what these are can help users avoid falling for them. typical social engineering. How to recognise a social engineering attack. the ability to recognize a social engineering attack hinges on sharpened situational awareness and honed critical thinking skills. in the nuanced world of cybersecurity threats, social engineering maneuvers through the gray areas of human interaction, making its detection both critical and challenging.
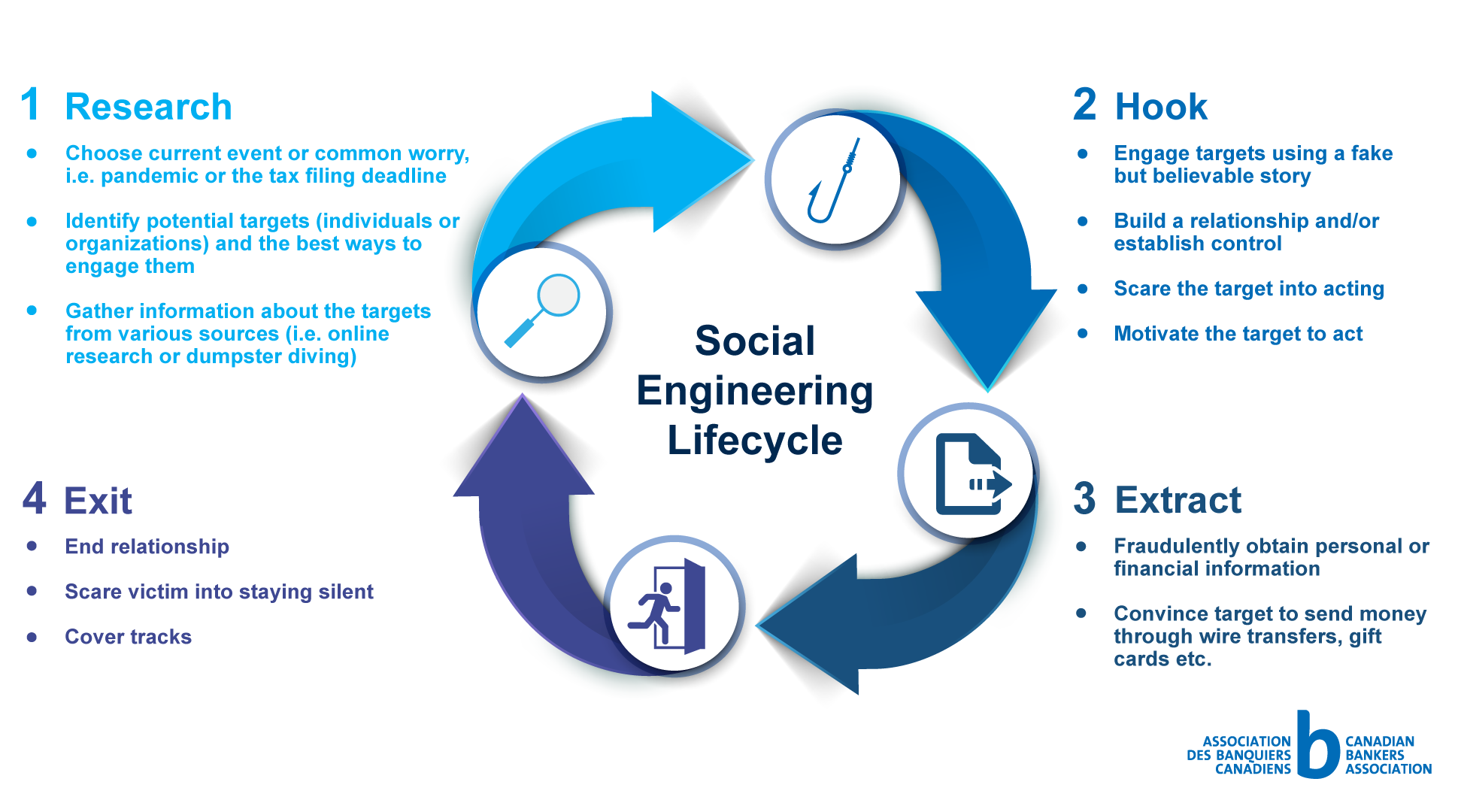
How To Identify And Avoid Social Engineering Attacks Neuron Computers Phishing is a form of social engineering. phishing attacks use email or malicious websites to solicit personal information by posing as a trustworthy organization. for example, an attacker may send email seemingly from a reputable credit card company or financial institution that requests account information, often suggesting that there is a. The threat landscape for social engineering attacks continues to evolve, requiring a proactive and adaptive approach to defense. to stay steps ahead of cybercriminals, businesses and organizations must be vigilant in recognizing and resisting these attacks to mitigate the short term and long term risks they pose. by educating employees and. In this article, we’ll discuss 13 common types of social engineering attacks, explain how they work, provide real life examples, and share best practices for preventing them. 1. phishing. phishing is one of the most common social engineering techniques. with phishing scams, attackers send emails that appear to be from reputable sources to. 1. phishing attacks: real life example: an employee receives an email purportedly from their company's it department, requesting login credentials for a system upgrade. guidance: verify the legitimacy of such emails by contacting the it department through official channels. 2.

Comments are closed.