How To Avoid Social Engineering Attacks
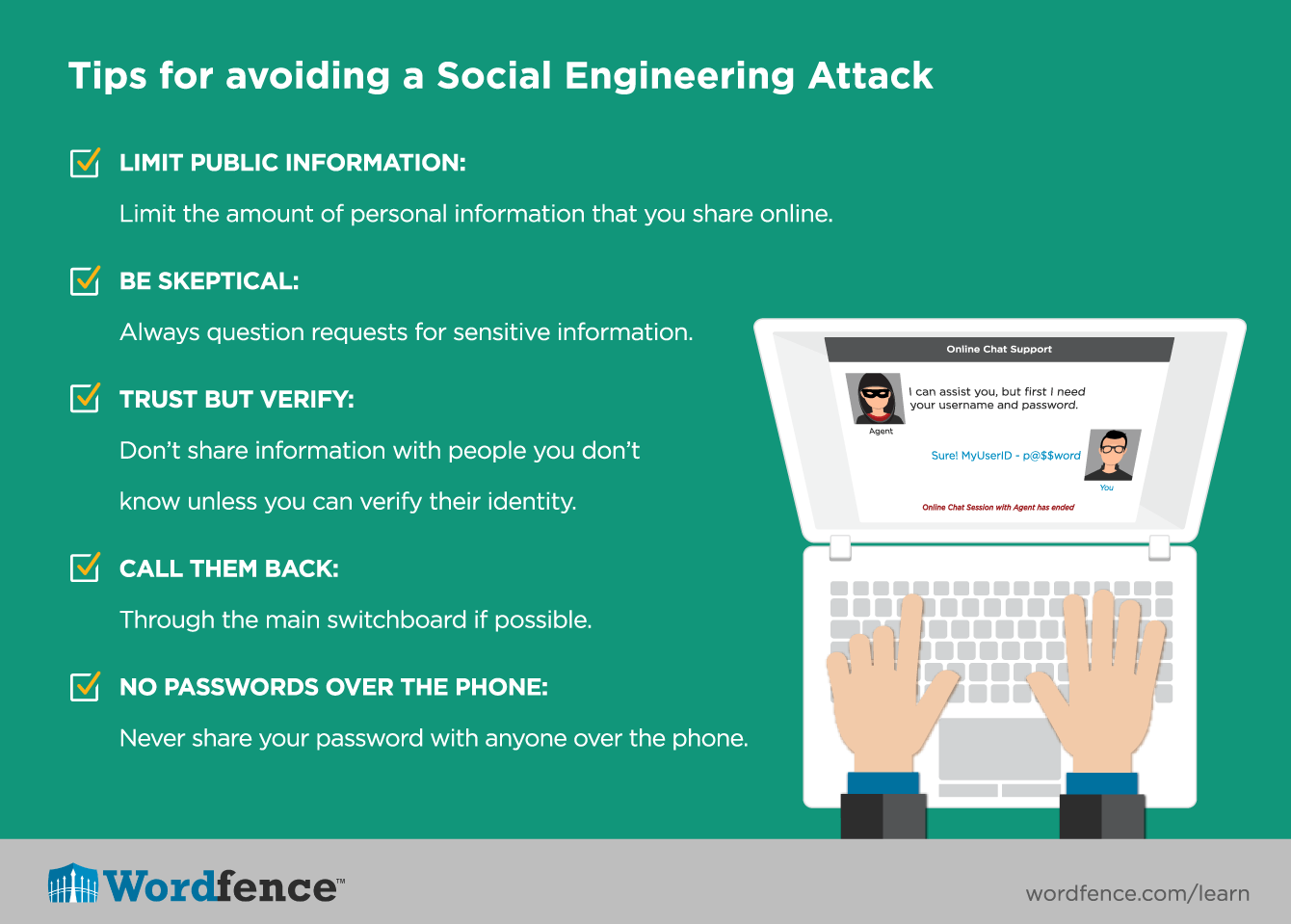
Understanding Social Engineering Techniques In just two quarters, the share of social engineering attacks out of all cyber security This is an arms race that no one can avoid being a part of What we can do is get smart about trust Cybersecurity researchers found new Iranian hacker networks targeting US political campaigns Kurt “CyberGuy" Knutsson reveals what you need to know and how to protect yourself
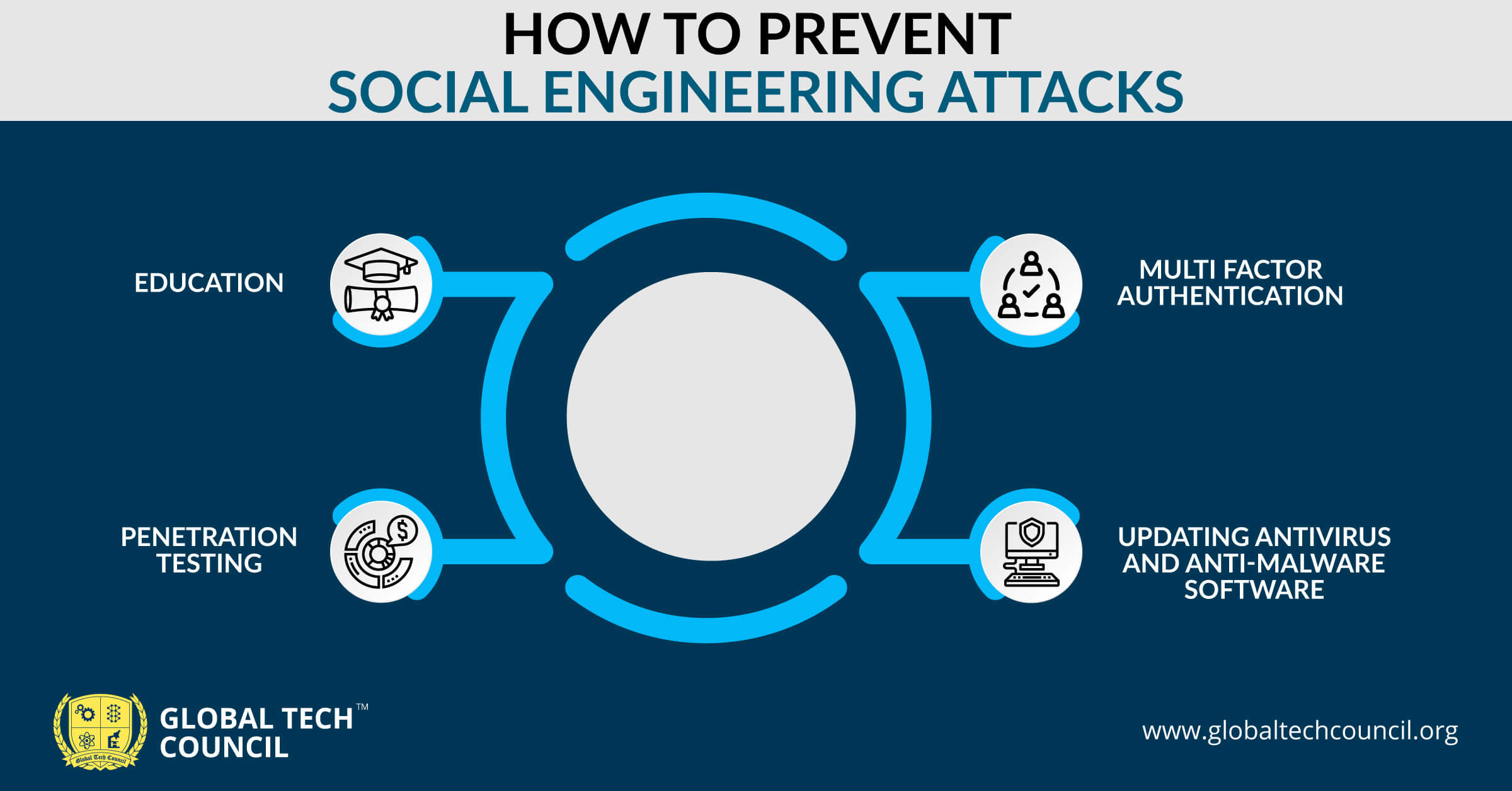
Social Engineering Attacks What They Are And Some Prevention Tips The FBI has warned crypto companies of sophisticated social engineering attacks by North Korean hackers targeting employees to install malware leading to crypto theft Local and state governments have increasingly embraced a multi-cloud strategy, providing them with greater resiliency than ever before and helping avoid vendor lock-in However, while distributing But God forbid, if it ends up happening to you then how would you know and what would you do? Panic, of course But then? Let us tell you some of the basics of how to know if your phone is hacked and Cybersecurity Awareness Month is approaching Any businesses and organizations, no matter how big or small, can be hacked in today's digital world

How To Stop Social Engineering Attacks 4 Ways To Prevent It But God forbid, if it ends up happening to you then how would you know and what would you do? Panic, of course But then? Let us tell you some of the basics of how to know if your phone is hacked and Cybersecurity Awareness Month is approaching Any businesses and organizations, no matter how big or small, can be hacked in today's digital world Cybercriminals are increasingly targeting healthcare organizations, but understanding the threats and regulations can help you safeguard sensitive patient data Experts link over 45 dolphin attacks in Japan to sexual frustration, with a lone male bottlenose dolphin targeting beachgoers By shifting to relatively low-tech communication devices, including pagers and walkie-talkies, Hezbollah apparently sought an advantage against Israel's well-known sophistication in tracking targets Sep 13, 2024 — When a patient needs a new heart valve, the current mechanical and tissue replacements each have strengths and weaknesses Now, a team of researchers believe they have found a

Comments are closed.