Hashing Algorithms And Security Computerphile
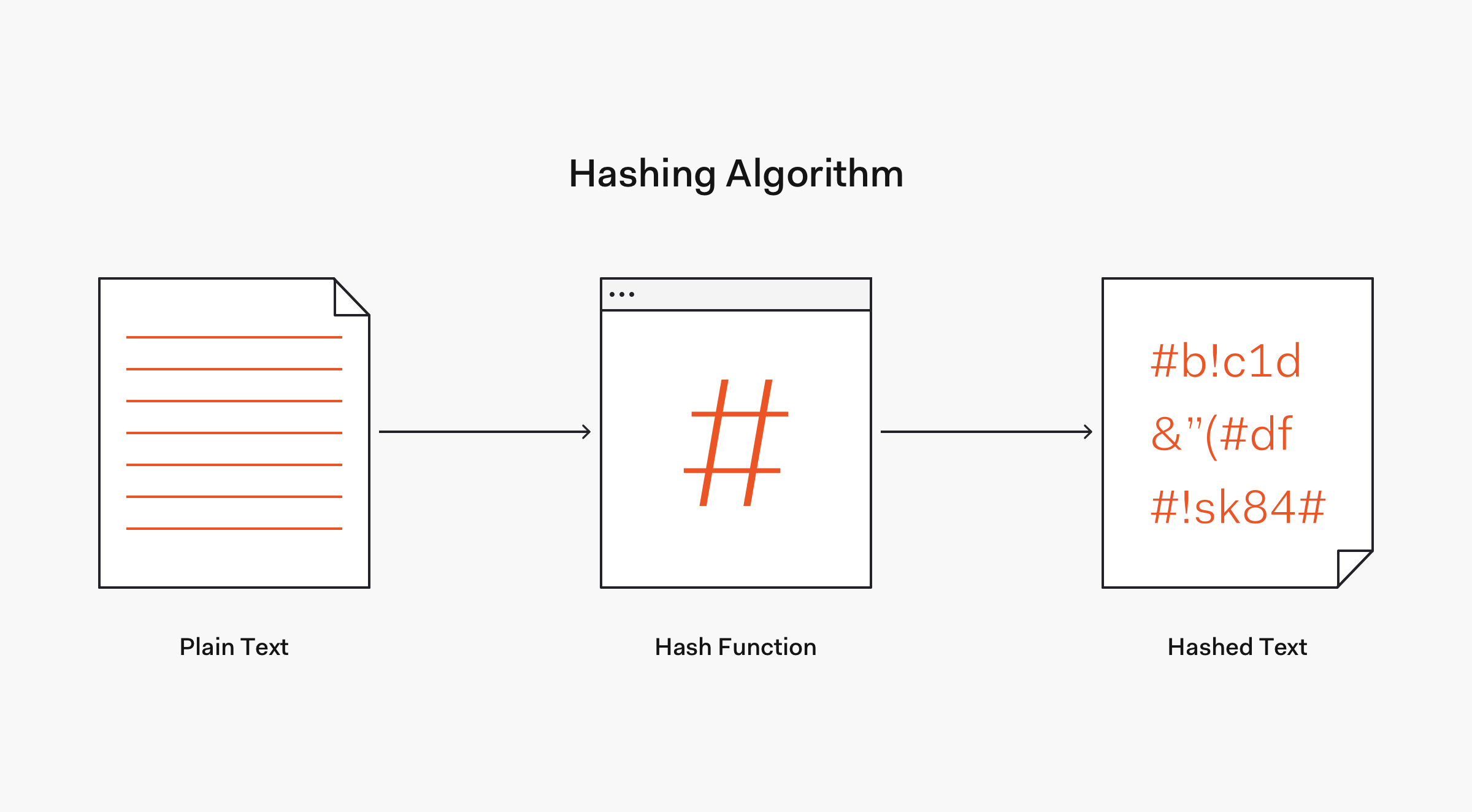
How To Hash Passwords One Way Road To Enhanced Security Audible free book: audible computerphilehashing algorithms are used to ensure file authenticity, but how secure are they and why do they keep. Secure hashing algorithm (sha1) explained. dr mike pound explains how files are used to generate seemingly random hash strings.extra bits: youtu.be f.

Everything About Secure Hashing Algorithm Sha Security Boulevard Secure hashing algorithm (sha1) explained. dr mike pound explains how files are used to generate seemingly random hash strings. sha: secure hashing algorithm. 1 other. contributed. secure hash algorithms, also known as sha, are a family of cryptographic functions designed to keep data secured. it works by transforming the data using a hash function: an algorithm that consists of bitwise operations, modular additions, and compression functions. the hash function then produces a fixed size string that. A hashing algorithm is a mathematical function that garbles data and makes it unreadable. hashing algorithms are one way programs, so the text can’t be unscrambled and decoded by anyone else. and that’s the point. hashing protects data at rest, so even if someone gains access to your server, the items stored there remain unreadable. Hashing algorithms and security explained. | video: computerphile what is hashing used for? hashing is primarily used for security purposes, and specifically those in cybersecurity. a hashed value has many uses, but it’s primarily meant to encode a plaintext value so the enclosed information can’t be exposed.
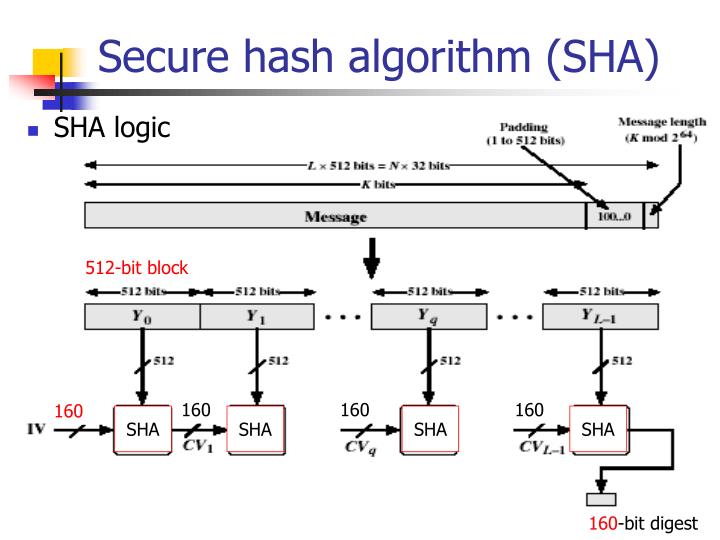
Ppt Sha Secure Hash Algorithm Powerpoint Presentation Id 6450319 A hashing algorithm is a mathematical function that garbles data and makes it unreadable. hashing algorithms are one way programs, so the text can’t be unscrambled and decoded by anyone else. and that’s the point. hashing protects data at rest, so even if someone gains access to your server, the items stored there remain unreadable. Hashing algorithms and security explained. | video: computerphile what is hashing used for? hashing is primarily used for security purposes, and specifically those in cybersecurity. a hashed value has many uses, but it’s primarily meant to encode a plaintext value so the enclosed information can’t be exposed. Secure hash algorithm (sha) is a versatile and useful cryptography technique and can ensure the data integration and verification, digital signature generation for documents and email and also secured and safe password storage and management. sha are available with different versions (sha 1, sha 256 and sha 3) and serves the purpose of. The secure hash algorithms are a family of cryptographic hash functions published by the national institute of standards and technology (nist) as a u.s. federal information processing standard (fips), including: sha 0: a retronym applied to the original version of the 160 bit hash function published in 1993 under the name "sha".
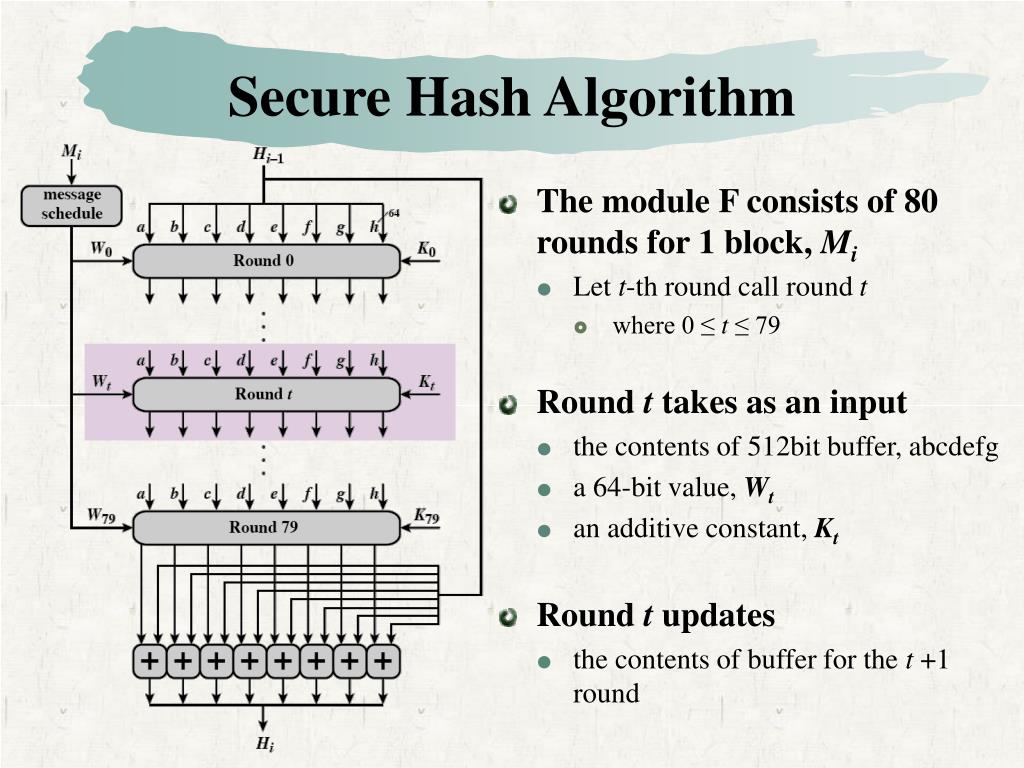
Ppt Hash And Mac Algorithms Powerpoint Presentation Free Download Secure hash algorithm (sha) is a versatile and useful cryptography technique and can ensure the data integration and verification, digital signature generation for documents and email and also secured and safe password storage and management. sha are available with different versions (sha 1, sha 256 and sha 3) and serves the purpose of. The secure hash algorithms are a family of cryptographic hash functions published by the national institute of standards and technology (nist) as a u.s. federal information processing standard (fips), including: sha 0: a retronym applied to the original version of the 160 bit hash function published in 1993 under the name "sha".

Comments are closed.