Figure 1 From Assertions And Protocol For The Oasis Security Assertion
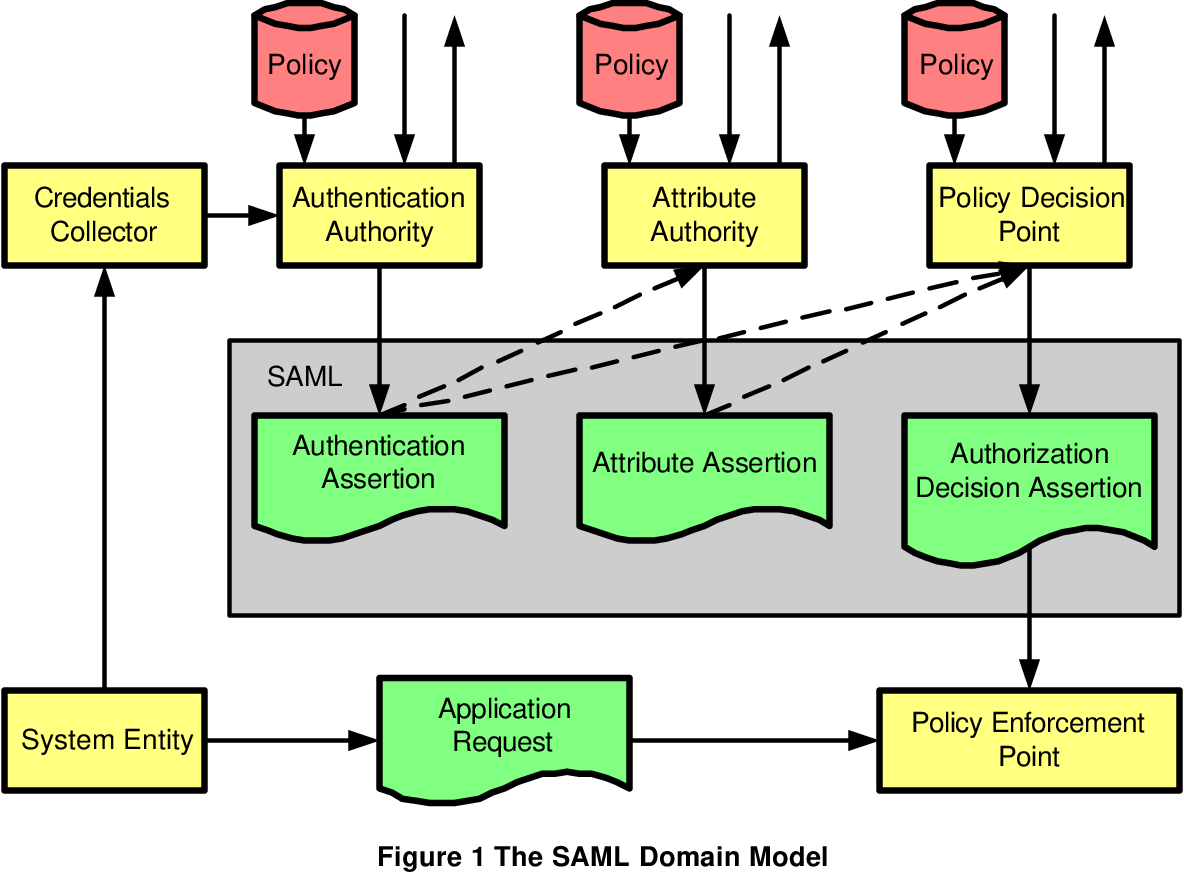
Figure 1 From Assertions And Protocol For The Oasis Security Assertion Hence, Paul D Williams argued that “security is therefore a powerful political tool in claiming attention for priority items in the competition for government attention” 1 In the context of The reunion that Oasis fans long hoped for (but never believed would happen) could be on the cards, with former frontman Liam Gallagher and his songwriter-guitarist brother Noel dropping hints

Pdf Assertions And Protocol For The Oasis Security Assertion Implementing comprehensive assertions traditionally involves and to achieve consistency by code generation Figure 1 XML structure overview III XML-BASED META LANGUAGE Current assertion Should a bronze medal count the same as a gold when determining who won the Olympics? What’s the best way to rank countries based on medal count? By The Learning Network Bomb threats and What is the best overall home security system? Home security systems help keep your home secure while you're away at work, on vacation or just peacefully sleeping at night From intruders to If a website supports security keys, you can enroll one for use with the account The key cryptographically proves its legitimacy using the FIDO authentication protocol Basically, instead of

Assertions And Protocols For The Oasis Security Assertion What is the best overall home security system? Home security systems help keep your home secure while you're away at work, on vacation or just peacefully sleeping at night From intruders to If a website supports security keys, you can enroll one for use with the account The key cryptographically proves its legitimacy using the FIDO authentication protocol Basically, instead of In the years since that fateful meeting, I’ve become PCMag’s expert on security, privacy, and identity protection, putting antivirus tools, security suites, and all kinds of security software This jailbreak is a pure software jailbreak for the Kindle Paperwhite 2, the Kindle Paperwhite 3, Kindle Touch, Kindle Voyage, and Kindle Oasis If you’re keeping track, that’s any 6th Several industry alliances have come together to define such standards, as shown in figure 1 UCIe is a comprehensive specification Die-to-Die Adapter Layer and Protocol Layer The UCIe interface Oasis fans have been expressing buyers' regret He told of receiving a sobering alert from his bank after splashing out a four-figure sum on four standing tickets for one of their gigs in

Comments are closed.