A Beacon In Lsass Top And Credential Dumping With The Download
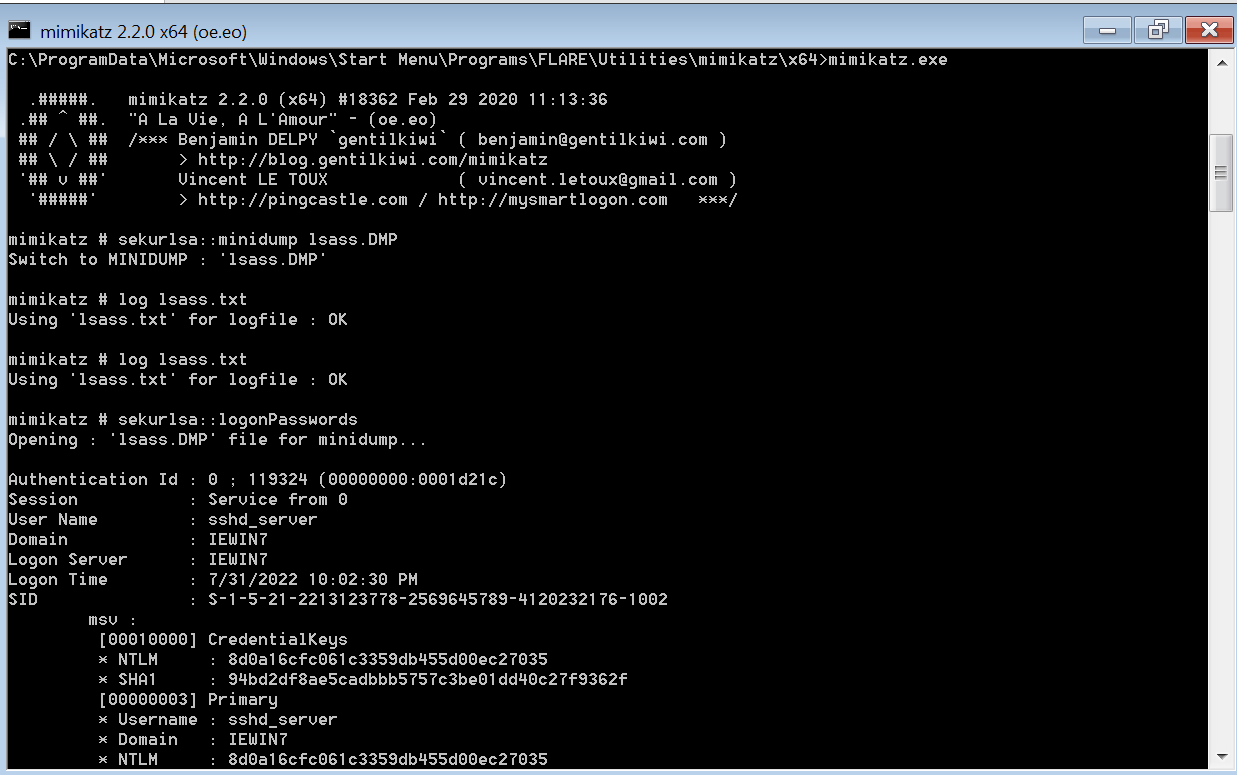
A Beacon In Lsass Top And Credential Dumping With The Download Lsass credential dumping is becoming prevalent, especially with the rise of human operated ransomware. in may 2022, microsoft participated in an evaluation conducted by av comparatives specifically on detecting and blocking this attack technique and we’re happy to report that microsoft defender for endpoint achieved 100% detection and prevention scores. As well as in memory techniques, the lsass process memory can be dumped from the target host and analyzed on a local system. for example, on the target host use procdump: procdump ma lsass.exe lsass dump. locally, mimikatz can be run using: sekurlsa::minidump lsassdump.dmp. sekurlsa::logonpasswords.
Lsass Dumping Techniques Hawkeye Adversaries may attempt to dump credentials to obtain account login and credential material, normally in the form of a hash or a clear text password. credentials can be obtained from os caches, memory, or structures. [1] credentials can then be used to perform lateral movement and access restricted information. Lsass process: lsass handles both local and domain credentials, managing in memory credential caches that include plaintext passwords, hashes, and kerberos tickets. dumping from lsass offers a more comprehensive set of credentials, including those of currently logged in users. this requires administrative access and is performed on a running. The continuous evolution of the threat landscape has seen attacks leveraging os credential theft, and threat actors will continue to find new ways to dump lsass credentials in their attempts to evade detection. for microsoft, our industry leading defense capabilities in microsoft defender for endpoint are able to detect such attempts. Users with system privilege can interact with the lsass.exe process and dump its memory. adversary use of lsass memory. since lsass memory contains valuable credentials, adversaries utilize various methods and tools to dump lsass memory and extract credentials: mimikatz: mimikatz is the most common tool for credential dumping. mimikatz can.

Dumping Credentials вђ Lsass Process Hashes Juggernaut Sec The continuous evolution of the threat landscape has seen attacks leveraging os credential theft, and threat actors will continue to find new ways to dump lsass credentials in their attempts to evade detection. for microsoft, our industry leading defense capabilities in microsoft defender for endpoint are able to detect such attempts. Users with system privilege can interact with the lsass.exe process and dump its memory. adversary use of lsass memory. since lsass memory contains valuable credentials, adversaries utilize various methods and tools to dump lsass memory and extract credentials: mimikatz: mimikatz is the most common tool for credential dumping. mimikatz can. Enter nanodump, a tool that capitalizes on the potential of beacon object files. with its .o file, nanodump can be used to bypass the latest windows defender's defenses and effectively dump the. Download scientific diagram | a beacon in lsass (top) and credential dumping with the minidumpwritedump bof which replicates the function with the same name (below) when using the same method with.

Dumping Lsass Ttp Credential Access в John S Infosec Notes Enter nanodump, a tool that capitalizes on the potential of beacon object files. with its .o file, nanodump can be used to bypass the latest windows defender's defenses and effectively dump the. Download scientific diagram | a beacon in lsass (top) and credential dumping with the minidumpwritedump bof which replicates the function with the same name (below) when using the same method with.

Comments are closed.